Single Sign On Citrix Workspace App
Citrix Federated Authentication Service (FAS) supports single sign-on to virtual apps and desktops in Citrix Workspace. Within each resource location, you can connect multiple FAS servers to Citrix Cloud for load balancing and failover purposes. You can use the same FAS server for both on-premises and Citrix Cloud with proper rule configuration. Citrix Single Sign On with Receiver and Receiver for Web. Workspace app for HTML5 is a way to connect to resources without the need to install a. You enable single sign-on with Citrix Gateway using the GPO administrative template. Open the Citrix Workspace app GPO administrative template by running gpedit.msc. Under the Computer Configuration node, go to Administrative Template Citrix Components Citrix Workspace User Authentication. Select Single Sign-on for Citrix Gateway policy.
SSO Overview
There are to ways you can use SSO in a Citrix 7.5+ environment using built-in Citrix technologies:
- SSO via Citrix Receiver for Web
- SSO via the Citrix Receiver client
Hi, Since it seams MS Teams optimization will not come to Thinos in the near future I’m trying out a Wyse 5070 with Windows Iot and WMS. I managed to upgrade Citrix Receiver to Workspace App 1911 from WMS, but I find no way to activate the Single Signon feature of Citrix Workspace. Hello, we have installed one XenDestops 7.16 Storefront Server and configured some Apps und the store. Our test Client runs with Windows 10 and Receiver 4.10. After the users boot their Clients and login to their clients with their ActiveDirectory Account, I dont want that they the storeweb site.
Depending on which method you choose the prerequisites differ, however not by much. Below are the prerequisites that are required for either method, meaning it doesn’t matter which method you choose the same prerequisites exist:
- Citrx Receiver must be installed on the client device with the SSON component installed
- Receiver for Web website must be in the Local Intranet Zone
- If using the Trusted Sites zone instead, Automatic logon with current username and password must be set in Trusted Sites zone (I will talk no further about using the Trusted Sites zone)
- Domain pass-through must be enabled on Receiver for Web via StoreFront console
- Requests sent to the XML service port on your DDCs must be trusted
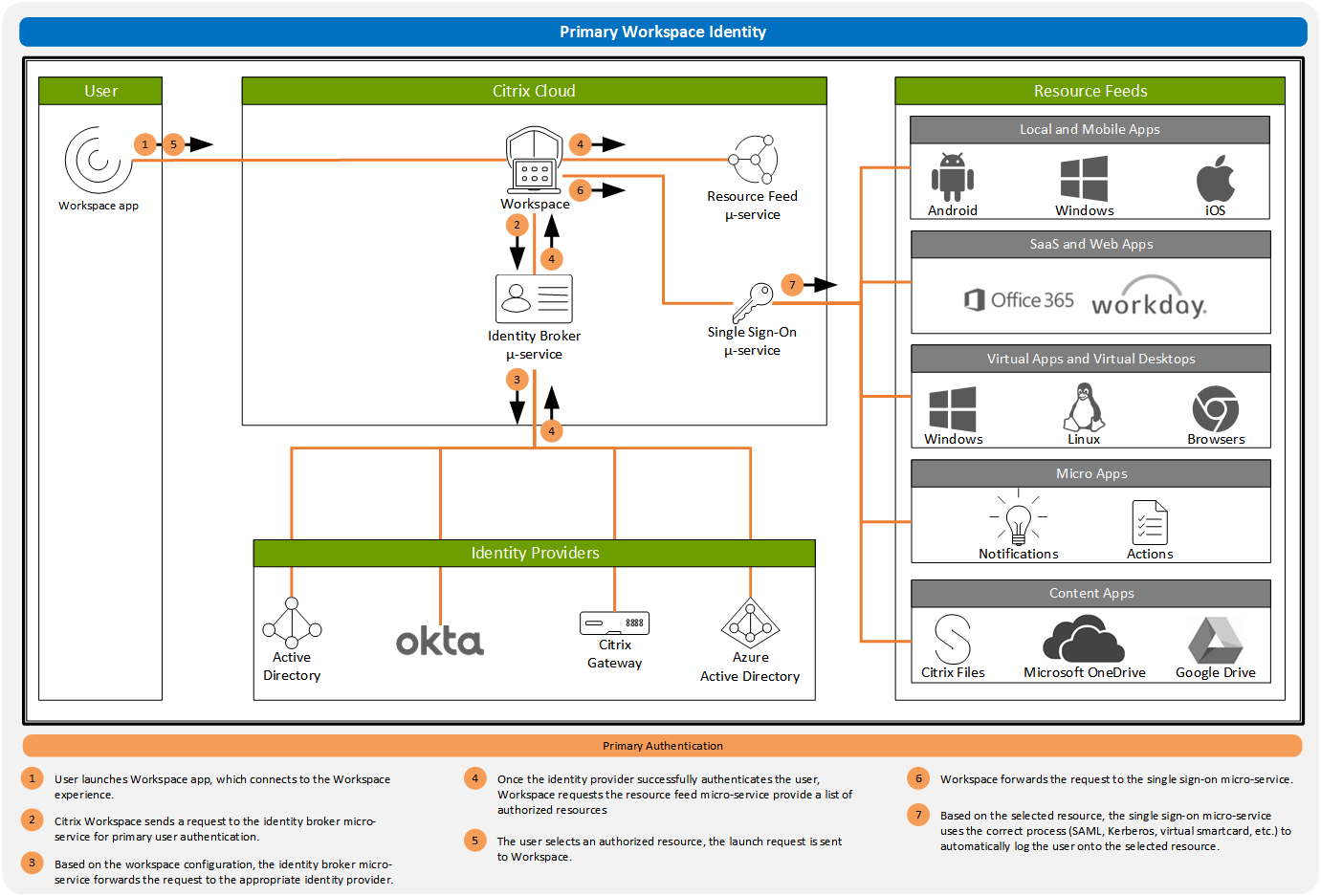
Now below are the remaining unique prerequisites/differences for each method.
Receiver for Web
- Always use Receiver for HTML5 must not be selected in StoreFront
- Internet Explorer must be used when accessing Receiver for Web
- Group Policies do not need created for Receiver for Web SSO
- The User Name and Password Receiver for Web authentication method should be disabled to avoid extra prompts which will later be explained
Receiver client
- Group Policies do need created for Receiver client SSO
Installing and configuring SSO (Receiver for Web):
- Citrix Receiver client must be installed on the end device. The SSO component is not required so a simple GUI or command line interface command can be used to install the client.
- Using StoreFront MMC, enable Domain pass-through on Receiver for Web
- Using StoreFront MMC, disable User Name and Password authentication against Receiver for Web
- Launch Internet Explorer on logon by placing a shortcut in the Startup folder C:ProgramDataMicrosoftWindowsStart MenuProgramsStartup. This should be done on the base/gold image
- Set Internet Explorers homepage to the Receiver for Web website address
- Create a GPO linked to all machnes participating in Citrix Receiver for Web SSO or use an existing policy
- Using the above created policy, edit the setting Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel to include the Receiver for Web website address in the Local Intranet zone
Decision: To get rid of the first-time logon prompt which will be shown later in this post, you need to disable User Name and Password authentication. Doing so partly reduces functionality:
- Non domain machines cannot authenticate to this Receiver for Web website
- Usrs can not log on using a set of credentials different than those they used to log on to their domain joined client device
Keeping the above restrictions in mind, a decision must be made to bring true SSO experience at the expense of reduced authentication ability, or accept that a prompt will be given to users on first log on to Receiver for Web in favour of keeping maximum authentication abilities. It is also possible to create a seperate Receiver for Web website for SSO users only, or create sites for non-SSO participants. This means you can configure seperate devices/users to point to specific Receiver for Web websites based on authentication needs.
Installing and configuring SSO (Receiver client)
- Citrix Receiver client must be installed on the end-device. The SSO component is required so a simple GUI or command line interface command can be used to install the client. A command line install if preferred because you can automate Citrix Store configuration. The following command at minimum is required to install Receiver client: CitrixReceiver.exe /includeSSON (tested on Receiver 4.3)
- Using StoreFront MMC, enable Domain pass-through on Receiver for Web
- Download and copy receiver.admx and receiver.adml template files to the PolicyDefinitions folder on a Domain Controller
- Create a GPO linked to all machines participating in Citrix Receiver client SSO or use an existing one
- Using the above created policy, edit the setting Computer Configuration -> Policies -> Administrative Templates -> Citrix -> Components -> Citrix Receiver -> Local User Name and Password enabling Enable pass-through authentication
- Using the above created policy, edit the setting Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel to include the Receiver for Web website address in the Local Intranet zone
The Receiver for Web logon prompt
Now that we have discussed the prompt and the advantages/disadvantages with enabling/disabling this feature, here below is a picture of what the prompt actually is and looks like.
When you have enabled Domain pass-through and User name and Password authentication on Receiver for Web, the first time a user logs on they get this prompt to either log on using the account used to sign on to the computer or to switch to the username and password logon screen. The user name and password logon screen gives the user the ability to authenticate with any set of credentials they have. Since I mention “first time” above, first time means the first time a user logs on to Receiver for Web on a device that they have never used before. The next time they use the same machine the same prompt does not appear. If you log off, you may also get the below message.
If the device is a thin-client with a write-based restrictive filter, the profiles may not be stored and as such the user is using that machine for the first time every time as far as the device is concerned after said device is restarted. This reduces the SSO experience, as the prompt requires manual input. Users wanting true SSO experience must disable User name and Password authentication. User name and Password authentication conflicts with SSO and is not required. A seperate Receiver for Web site must be created for users who do require the User name and Password authentication method. User name and Password is enabled by default when you install Citrix StoreFront.
The User Name and Password authentication method
Configuring SSO for Receiver client
Citrix Workspace Sso
Now that we have covered the theory, I will walk through configuring SSO for Receiver client. I won’t go through SSO with Receiver for Web but it is just as similar to configure.
Install Citrix Receiver on the client device with SSON component included. I am using a command to install. The command automatically configures the store.
You could also enable SSO by checking the box on newer versions (4.3+) if you prefer however you will have to manually configure the store or use the Receiver ADMX templates with Group Policy.
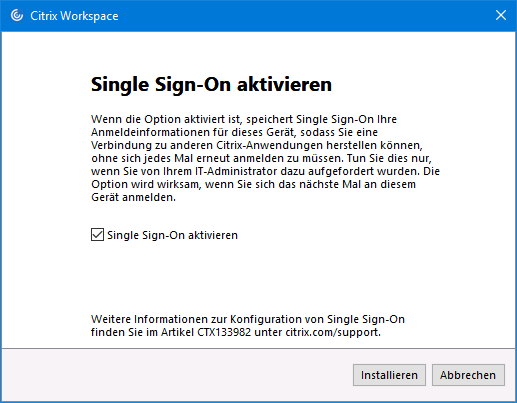
Insert the Receiver for Web site in the Local Intranet Zone. If using the Trusted Sites zone instead, Automatic logon with current username and password must be set in the Trusted Sites zone. In most cases you will use the Local Intranet zone. This is best done via GPO.
Values:
- Intranet Zone = 1
- Trusted Sites = 2
If using the Trusted Sites zone, enable Automatic logon with current username and password.
Enable Domain pass-through on Receiver for Web via StoreFront console and remove other authentication method(s). Pass-through from NetScaler Gateway can be enabled, however User name and password should not.
On your DDCs requests sent to the XML service port on your DDCs must be trusted, so run the following command:

Configure Group Policy to enable pass-through authentication on Receiver. You will need to have imported the Receiver.admx and Receiver.adml files to the Group Policy Central Store.
Outcome
Now if you open the Citrix Receiver client on your device, it should not ask to configure the store or ask for credentials. Instead, you will be passed through to StoreFront and presented with your subscribed applications and desktops.
Be aware after installing Receiver you must log off/on to your client device for the SSONSVR.EXE process to start and capture your credentials.
Additional feature – Desktop Lock
You can also turn your PC/Thin Clients in to kiosk type machines using what is called Citrix Desktop Lock. When a user logs on to their device the Citrix desktop automatically launches in full-screen mode and if the user disconnects or logs off the Citrix desktop the user is automatically logged off the local device. This is great in a VDI environment if you want to bring a true no-touch experience to your users. You can download Desktop Lock from the Citrix website.
Once downloaded launch the Citrix Desktop Lock software on an SSON configured client device.
Click Close once the software has installed.
Restart the client device.
Now log on as a standard user who has one Citrix desktop assigned to them.
Desktop Lock automatically launches the desktop in full screen.
The Desktop Viewer toolbar has some missing buttons to prevent the user from minimizing the desktop for example.
When the user disonnects or logs off, the local client device is also logged off. This helps secure the device and not leave any unattended workstations logged on.
If you need to control the local device yourself, log on as a user who is a Local Administrator of that machine and you will be presented with the below prompt.
After clicking OK you can access the local desktop to perform management tasks.
Troubleshooting SSO
- The SSONSVR.EXE process must be running on your client device
- Ensure you have met all the prerequisites stated above for your SSO method (Receiver client/Receiver for Web)
- Using an SSO configured device go to https://yourstorefrontserver.domain.com/citrix/storename/domainpassthroughauth/test.aspx. The web address I would go to is https://storefront.citrixpro.co.uk/citrix/cpsweb/domainpassthroughauth/test.aspx and if SSO is correctly configured you should see results similar to the below. (Included in StoreFront 2.5)
- Restart the client device (requirement after Receiver install with SSON)
Receiver 4.5 (released September 2016):
New with Citrix Receiver for Windows 4.5 is the Configuration Checker tool which performs various checks against the prerequisites needed for SSO to work. Open Advanced Preferences by right-clicking the Receiver icon in the system tray. Click Configuration Checker.
Tick SSONChecker and click Run.
As you can see a number of checks have been performed with one failure.
Looking closer at the failure alert we can see the Single Sign-on process is not running. After installing the SSON components you only need to log off/on for the process to run. In this case, I deliberately left out the SSON component so it is not installed at all. Click on Save Report to save the results to .TXT.
Heres a look at the results .TXT file.
I’ve now ran the SSON Checker on a machine that is properly configured for SSO. As expected, all checks have passed.
Receiver SSON logging:
You can enable SSON logging which may be help in identifying an issue.
Add a the following values to HKLMSoftwareCitrixInstallSSON (32bit) or HKLMSoftwareWOW6432NodeCitrixInstallSSON (64bit).
Citrix Workspace App Single Sign On
REG_SZ DebugEnabled = true
REG_SZ LogPath = Path location
When you log off and on again log files will be created relating to SSON.
Citrix Workspace App Disable Single Sign On
The trace-pnsson.log file shows information such as the credentials captured and packaged by SSON.
