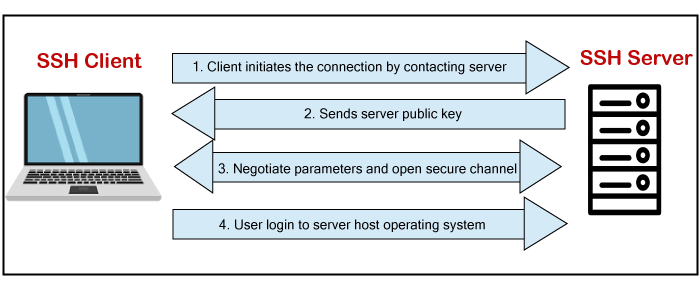
Open Ssh Connection
Last updated: 19 Mar, 2021 Copy Copied You can use MobaXterm to connect from your local Windows system to NAS systems via , as an alternative to Cygwin/OpenSSH. MobaXterm includes a built-in X11 client, and has the ability to forward X11 from NAS systems back to your local system. You can also use it to create VNC sessions. Note: MobaXterm is only useful if you are using to connect to NAS systems. It cannot be used for remote transfers utilizing the Secure Unattended Proxy () with Shift or other commands. Downloading and Installing MobaXtermMobaXterm Home Edition is available for free, and should be sufficient for most users. If you have admin privileges on your local system, you can install a full version (Installer Edition) with Start menu support. If a full software installation is not possible, you can use the standalone version (Portable Edition). A paid version (MobaXterm Professional) is also available. You can download them here: https://mobaxterm.mobatek.net/download.html Connecting to NAS SystemsIf you do not have Passthrough set up, use Method 1 to first connect to a secure front end (SFE), then log into a Pleiades or Lou front end (PFE or LFE). If you have Passthrough set up, you can connect directly to a PFE or LFE using Method 2. Method 1: Creating a New Session to Connect to an SFEComplete these steps to create a new session to connect to a secure front end (SFE).
Once you are connected to the SFE, you can use the Linux command line to into a PFE or LFE. Enter your NAS password when prompted. Note: After you change your NAS password, you might have to remove your old password stored in MobaXterm before you can enter the new password when prompted. To remove your old NAS password, go to the the MobaXterm Settings dropdown menu and select Configuration; then select MobaXterm passwords management; then select the password that was changed, and click Delete. Method 2: Creating a New Session to Connect Directly to a PFE or an LFEIf you have Passthrough set up, complete these steps to connect directly from your Windows system to a PFE or LFE:
MobaXterm will log into the NAS system that you set in Step 3 (in this example, pfe24): Duplicating a Login SessionIf the original login session is still running, you can duplicate it to create new login sessions. Click the Sessions section, and select the session you want to duplicate: A new xterm tab will be created and logged in. No passphrase or passcode will be needed: Note: To connect to other NAS systems, (for example, pfe26 instead of pfe24) you must start a new connection. You will be prompted for your passphrase and RSA SecurID passcode. Running a Graphical Application with VNCIf you enabled X11-forwarding in the Advanced settings tab when you initiated your session, you can run X and OpenGL applications. For example: However, we highly recommend using Virtual Network Computing (VNC) for graphical work on NAS back to your local machine, as it is generally faster than X11 forwarding. Using an X11 alternative like VNC in MobaXterm requires two tunnels through the NAS SFEs. To run VNC, you will need to do the following:
Sample Setup for Using VNC on MobaXtermIn this example, forwarding is enabled between port 5901 of the local machine and port 5901 on pfe26, where a VNC server is running with a tunnel that passes through the SFE on port 6901. Note: These port numbers will be different in your case, depending on which ports VNC is listening on and which PFE you are running on. This example was created as follows: In the main MobaXterm client window, click the Tunneling icon to open the MobaSSHTunnel window. Then, click New tunnel and create Tunnel 1 and Tunnel 2. To create Tunnel 1: To create Tunnel 2: Once Tunnel 1 is started, then start Tunnel 2. Both will prompt for the RSA SecurID passcode and your NAS password, as MobaXterm doesn't allow for keys when tunneling. Now, you can start a local VNC viewer on your local system, pointing at port 5901. |
SSH Timeouts
Openssh For Windows 10 64 Bit
Hello I accessed my server with ssh one time on from Ubuntu16.04 But when tried to connect next time I goy this error 'Could not open a connection to your authentication agent' after executing. I have been ssh'ing to this computer (also Ubuntu 16) for months, today it's not working.running ssh -v ip yieldsOpenSSH7.2p2 Ubuntu-4ubuntu2.4, OpenSSL 1.0.2g 1 Mar 2016debug1: Reading. Is your OpenSSH server connection drops out after few minutes? Here is how to increase ssh connection time out to fix this annoying problem on Linux/Unix. Allows you to open a remote folder on any remote machine, virtual machine, or container with a. The easiest method to set up SSH connection to is.
When using default configuration on Ubuntu, you might experience SSH Timeouts (i.e. the console you are using to connect to a remote server will seem to freeze) after a few minutes of lack of activity.
Postfix Connection Timed Out
This is annoying because you need to open a new console instance and reconnect and perform any other steps you need before connecting.
Since using SSH to connect to remote servers is very common and linux being as old as it is, you would think that someone somewhere would have provided a solution for this problem by now; you'd be right.
Configuration
To increase the time a connection stays open you need to add configuration both to the client and the server

Client side
In the server/computer you are connecting from
Open file /etc/ssh/ssh_config and set directive ServerAliveInterval to a value like 60:
This causes your SSH client to send keep-alive messages every 60 seconds so that the server doesn't drop your connection.
Server-side
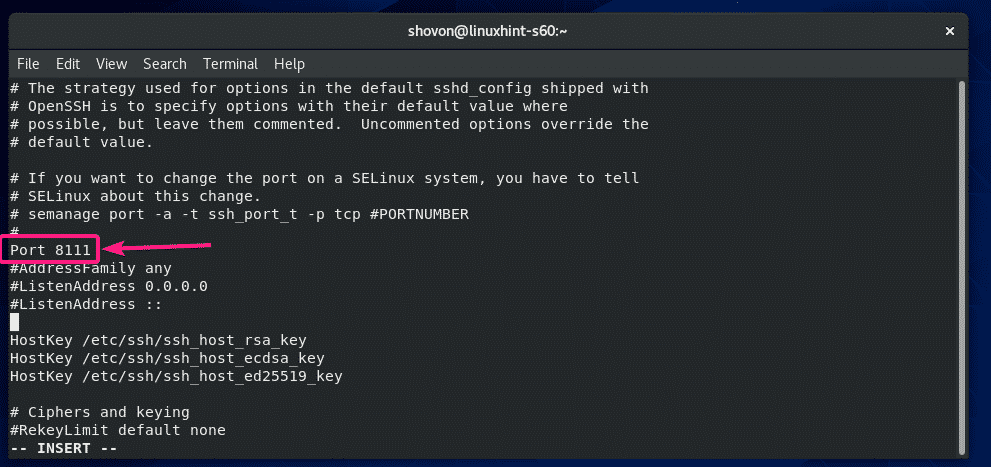
In the server you are connecting to
You must also configure the SSH remote Server you are connecting to.
Open file /etc/ssh/sshd_config and add these configurations1 at the end of the file.
Restart the ssh server so that changes take effect:
Open Ssh Connection Windows
Footnotes
Openssh Download
1: These are conservative settings that will make your SSH Server disconnect after (600 * 10 = 6000) seconds of user inactivity. Customize these if you need more.
